TikTok accounts have become prime targets for cybercriminals. Understanding their techniques is essential to protect your presence on the platform.
Discover available solutions to test TikTok account security.
This guide is for educational purposes only, aimed at informing you about TikTok security risks. Any unauthorized use of this information to access accounts is strictly prohibited and punishable by law.
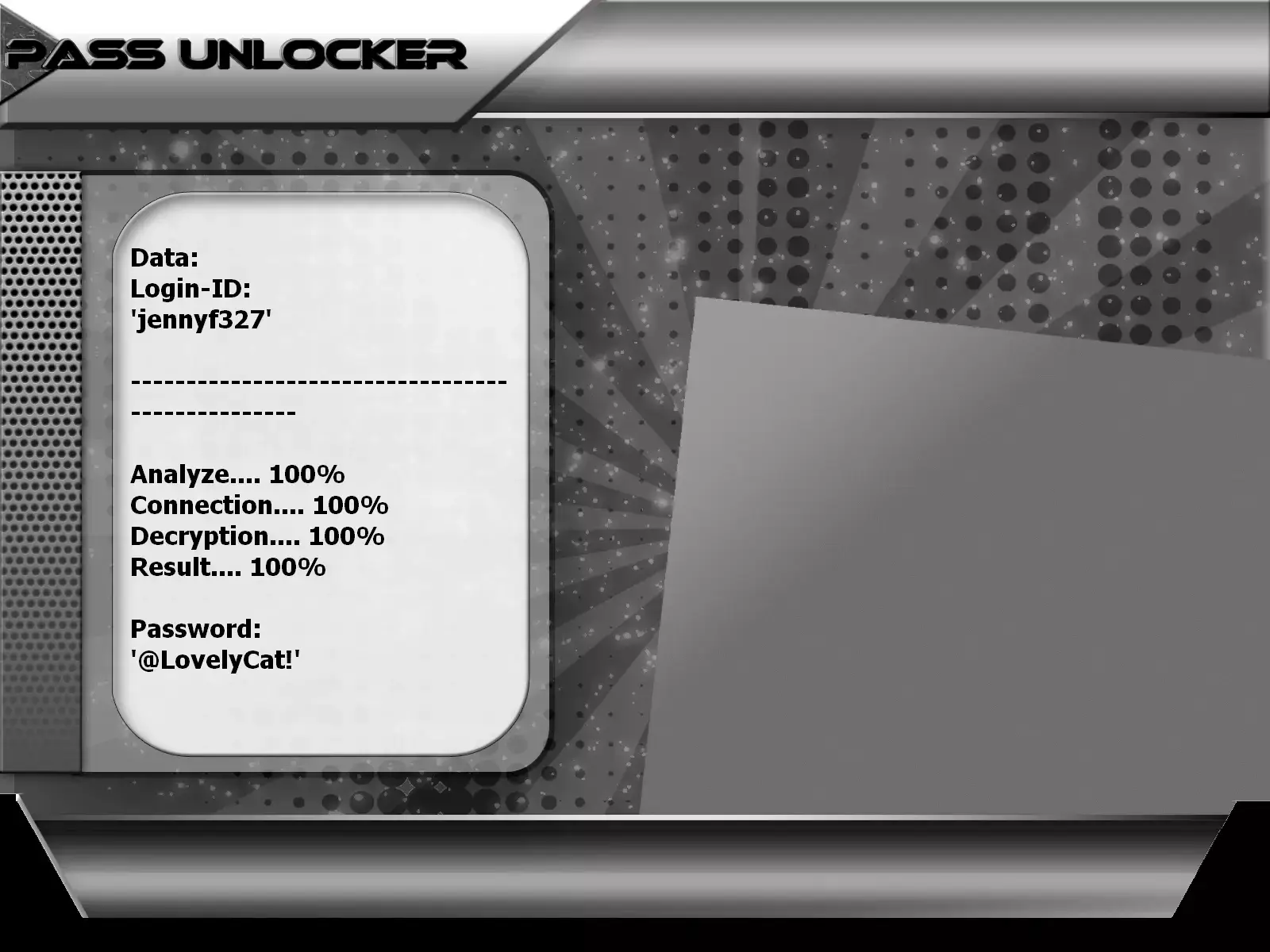
PASS UNLOCKER is a specialized application that decrypts access to a TikTok account using a username, phone number, or associated email address.
1. Download the application from the official website: https://www.passwordrevelator.net/en/passunlocker
2. After installation, enter the TikTok username, email address, or phone number linked to the account.
3. Launch the analysis. PASS UNLOCKER will generate account access credentials within minutes.
The application works without limitations and can be used on as many accounts as needed.
Learn the most commonly used strategies by cybercriminals to hack TikTok accounts and how to effectively counter them.
Sophisticated phishing techniques specifically designed to deceive TikTok users and steal their credentials.
Interception of active login data (cookies, tokens) to hijack your session and access your account without a password.
Systematic exploitation of user password weaknesses (low complexity, reuse across services).
Targeted manipulation of users into voluntarily disclosing credentials or performing compromising actions.
Sophisticated methods used by experienced cybercriminals specifically targeting high-value accounts.
Discovery and use of flaws in TikTok’s programming interfaces (APIs) to illegally access account data, modify settings, or post content.
Development of tools or apps promising advanced analytics, artificial follower growth (bots), or free premium features—but actually stealing your OAuth access tokens.
A technique to fraudulently transfer your phone number to a SIM card controlled by the attacker, allowing them to intercept SMS verification codes (2FA) and reset your password.
Proactive strategies and concrete security measures to durably secure your presence and data on TikTok.
Always enable two-step verification. Prefer an authentication app (Google Authenticator, Authy) over SMS, which is more vulnerable. Also link a backup email.
Use a password manager to generate and store a complex, long (14+ characters) password that is absolutely unique to TikTok. Never reuse passwords.
Regularly check the "Security and login" section in settings to review connected devices, login history, and revoke any suspicious activity.
Protecting your TikTok account is a crucial investment in your digital capital. By thoroughly understanding hacker methods and implementing layered security strategies, you make compromise extremely difficult. Our Lifee expert team can assist you with a complete digital security audit, advanced account configuration, and training on best practices.
Contact us now for a personalized, no-obligation TikTok account security audit.
Everything you need to know to effectively protect your TikTok account from hacking and intrusions.
Several unmistakable signs should immediately alert you:
Three fundamental pillars—with two-factor authentication (2FA) as the cornerstone:
Don’t panic—follow this step-by-step recovery procedure:
Exercise caution. Here’s how to assess the risks:
A popular account holds multiple types of value for cybercriminals:
This involves a trade-off between security and risk:
TikTok has implemented several integrated security layers:
Important: These protections are complementary but do NOT replace individual security best practices (strong password, 2FA).