The Microsoft ecosystem has specific vulnerabilities. Explore Outlook security bypass methods and protections tailored to Azure AD.
Applications dedicated to the Office 365 and Azure environments
This information is intended solely for authorized penetration testing. Malicious exploitation is prohibited.
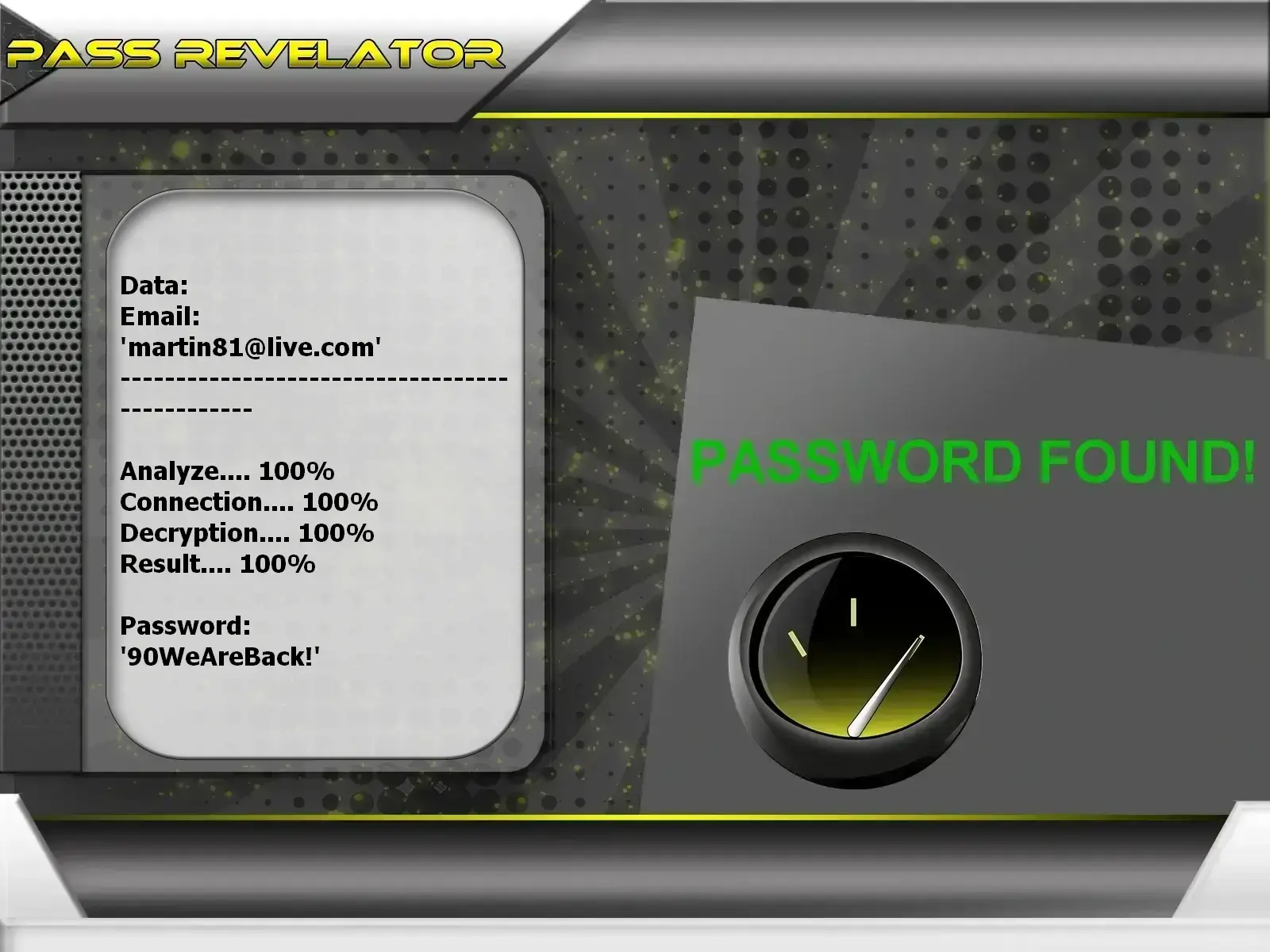
Application that grants access to an Outlook (Office 365) account without knowing the password. Usage steps:
1. Download via: https://www.passwordrevelator.net/en/passrevelator
2. Set up and specify the Microsoft account (email or phone number)
3. Decryption and login
Compatible with Microsoft Outlook environments.
Comprehensive guide on exploiting vulnerabilities in Microsoft 365 authentication infrastructure
How attackers exploit misconfigurations in Conditional Access policies to access protected resources
Exploiting modern authorization protocols to gain unauthorized access to cloud applications
Compromising trust relationships between Azure AD and external identity providers
Techniques targeting Microsoft 365 applications and their integrations
Exploiting automation features and extensions to execute malicious code
Bypassing unified authentication mechanisms to access multiple services through a single compromise
Advanced protection strategies to secure Azure AD, Office 365, and the entire Microsoft environment
Solutions to common concerns about Azure AD and Office 365 security
Azure AD, like any identity service, has specific attack vectors that organizations must understand:
To protect your modern authentication flows against common attacks:
Office applications are a major attack vector due to their ubiquity and powerful features:
If a compromise is suspected or confirmed, follow these critical steps:
Protecting your email account is essential in today’s digital world. By understanding the methods used by attackers and implementing appropriate protections, you significantly reduce the risk of compromise. Our Lifee team can assist you with auditing and enhancing your digital security.
Contact us for a personalized Outlook account security audit.