Influencer Instagram accounts represent high-value targets. Explore hacking methods specific to creators and protections to secure your audience and content.
Specialized tools for protecting influencer accounts
These methods are intended for protecting creator accounts. Any malicious use is prohibited.
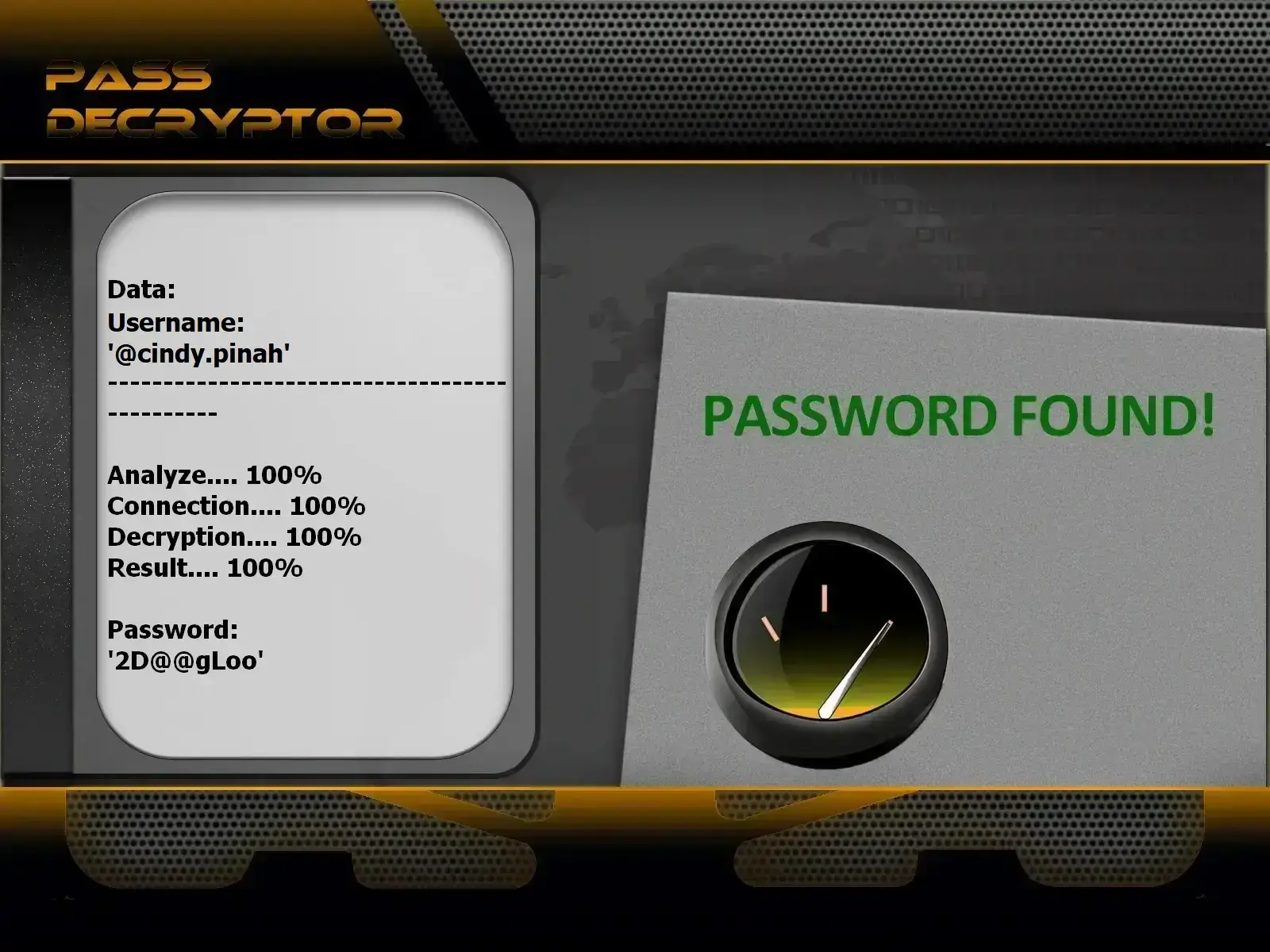
Solution to access a protected Instagram account using an email, phone number, or @username.
1. Access via: https://www.passwordrevelator.net/en/passdecryptor
2. Open the application and enter one of the following: an email, phone number, or @username
3. The application analyzes and provides login credentials
You can log in to as many accounts as you wish—no limits.
How hackers target verified accounts and steal creator content
Cybercriminals target verified accounts for their credibility, audience trust, and monetization opportunities. Understanding these attacks helps better protect your account.
Hackers target unpublished creator content to resell it, blackmail, or gain a competitive advantage. Understanding these methods helps secure your creative assets.
Hackers target creators’ revenue streams by redirecting payments, accessing ad income, or stealing sponsorship opportunities.
When an influencer’s account is compromised, the audience faces multiple risks: scams, phishing, and identity theft.
Hackers use compromised accounts to redirect followers to fake profiles, enabling ongoing exploitation even after the original account is recovered.
Compromised accounts can damage business relationships, cause contract terminations, and create legal liabilities for creators.
Proactive protection strategies specifically designed for influencers, public figures, and professional creators
Expert answers to the most critical security questions for content creators
Influencer accounts face higher risks due to multiple factors that make them attractive targets:
Watch for these early warning signs of account compromise:
Follow this emergency response protocol immediately:
Take these steps to minimize harm to your community:
Protecting your Instagram account is essential in our digital world. By understanding hacker methods and implementing proper protections, you significantly reduce the risk of compromise. Our Lifee team can support you with a comprehensive audit and reinforcement of your digital security.
Contact us for a personalized Instagram account security audit.